Proxmox & ACME
I just started experimenting with Proxmox VE, which I guess makes me the last homelabber on the Internet to do so1. One of the first things I wanted to fix was it’s self-signed certifiate, replacing it with my internal self-signed certificate authority, due to reasons.
As it turns out, Proxmox is just Debian with an Ubuntu kernel. That means that importing my local certificate authority is easy – just copy it over, place it in the right holder and ask Debian to index it! You can also use the same procedure with the ‘real’ ACME endpoints, but then there’s no need to import any local certificate authority.
It is worth noting that it’s not possible to change the port the web
UI is running on – it’s going to be :8006 unless you front it with
a reverse proxy or such2.
Preparations – install local CA #
First we copy the root CA:
# From my workstation, copy the certificate over
scp rootCA.crt root@pve01.exampel.com:/root
Then, on the host, we import and test the certificate:
# On the PVE node
cp /root/rootCA.crt /usr/local/share/ca-certificates/
update-ca-certificates
# Finally, test that curl can use the CA
curl https://ca.example.com/acme/acme/directory
That curl call should not throw a certificate error. If it did,
make sure your CA is in the right format, that it’s the right
certificate and so forth.
Setup Proxmox ACME HTTP-01 client #
This can be done in two ways – either by using the UI, or by using the CLI. Since we are already logged in on the host console we might as well use the CLI:
root@pve:~# pvenode acme account register default your.email@example.com
Directory endpoints:
0) Let's Encrypt V2 (https://acme-v02.api.letsencrypt.org/directory)
1) Let's Encrypt V2 Staging (https://acme-staging-v02.api.letsencrypt.org/directory)
2) Custom
Enter selection: 2
Enter custom URL: https://ca.example.com/acme/acme/directory
Now you should have an ACME account called ‘default’ defined in PVE. You can check this in the UI under Datacenter -> ACME, there should be an account listed.
Request certificate #
Due to reasons I did this part in the UI.
- Datecenter -> pve -> System -> Certificates
- Under ACME, press Add, use Challenge Type HTTP and insert the internal FQDN the host uses (pve.example.com) as Domain
- Finally, press Order Certificates Now
Once the ACME challenge is solved, you should find a new certificate
listed in the same view, mine is called pveproxy-ssl.pem in the
screenshot below:
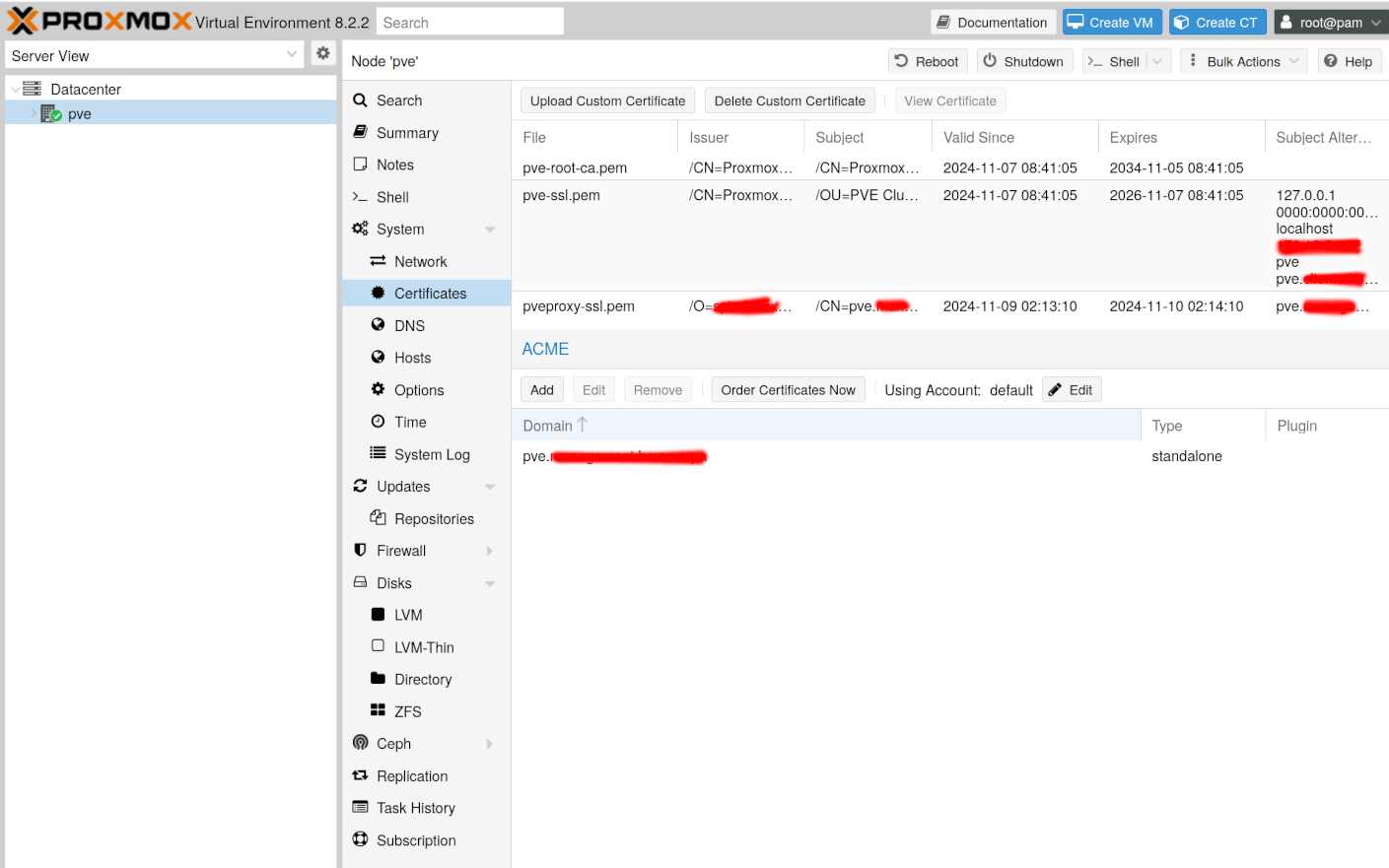
There you have it, a freshly minted internal certificate!
I’ve just used plain old
virsh, some Incus and Docker/Podman on Ubuntu/Debian and jails andvm-bhyveon FreeBSD. After starting labbing some with Incus/LXD I realized that using LXD containers on Proxmox might be interesting to test, and here we are! ↩︎Please don’t spin up a reverse proxy on the PVE node and use that to change the port – what if that reverse proxy VM/container won’t start, how do you troubleshoot and fix that? ↩︎